Introduction
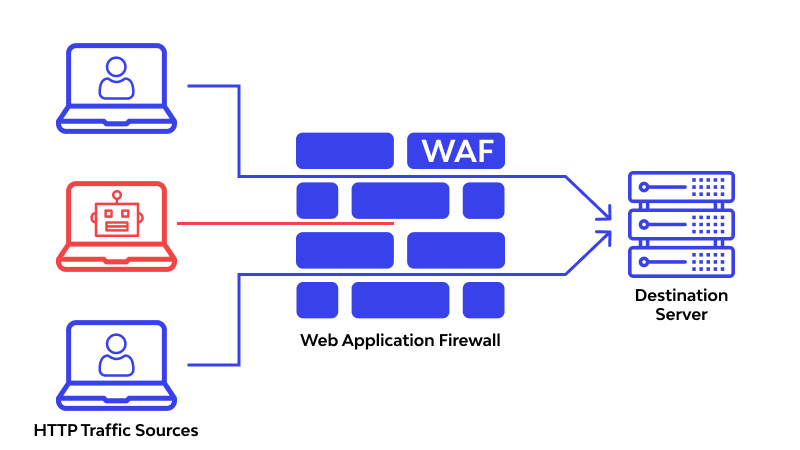
Bots are everywhere on the internet—some are helpful, like search engine crawlers, but many are harmful. Malicious bots scrape data, perform credential stuffing, launch DDoS attacks, and more. That’s where a Web Application Firewall (WAF) comes in. A WAF can effectively distinguish between human users and bots, helping protect your web application from automated threats.
What Is Bot Traffic?
Bot traffic refers to any non-human request made to your web server. This can be beneficial (like Googlebot indexing your site) or harmful (like bots attempting to brute-force login credentials). Differentiating between good and bad bots is key to maintaining both performance and security.
How WAFs Detect Bot Traffic
Modern WAFs use a variety of techniques to detect and categorize bot traffic:
- User-Agent Analysis: WAFs analyze the "User-Agent" header to identify known bots or spoofed identifiers.
- IP Reputation: IP addresses are checked against threat intelligence feeds and known botnet sources.
- Behavioral Analysis: WAFs monitor request patterns—bots often make rapid, repetitive requests that differ from human behavior.
- JavaScript Challenges: Humans can complete JavaScript-based tasks (like rendering), whereas bots typically fail or bypass them.
- CAPTCHA Enforcement: Conditional CAPTCHA challenges are used to confirm whether a client is a bot or a human.
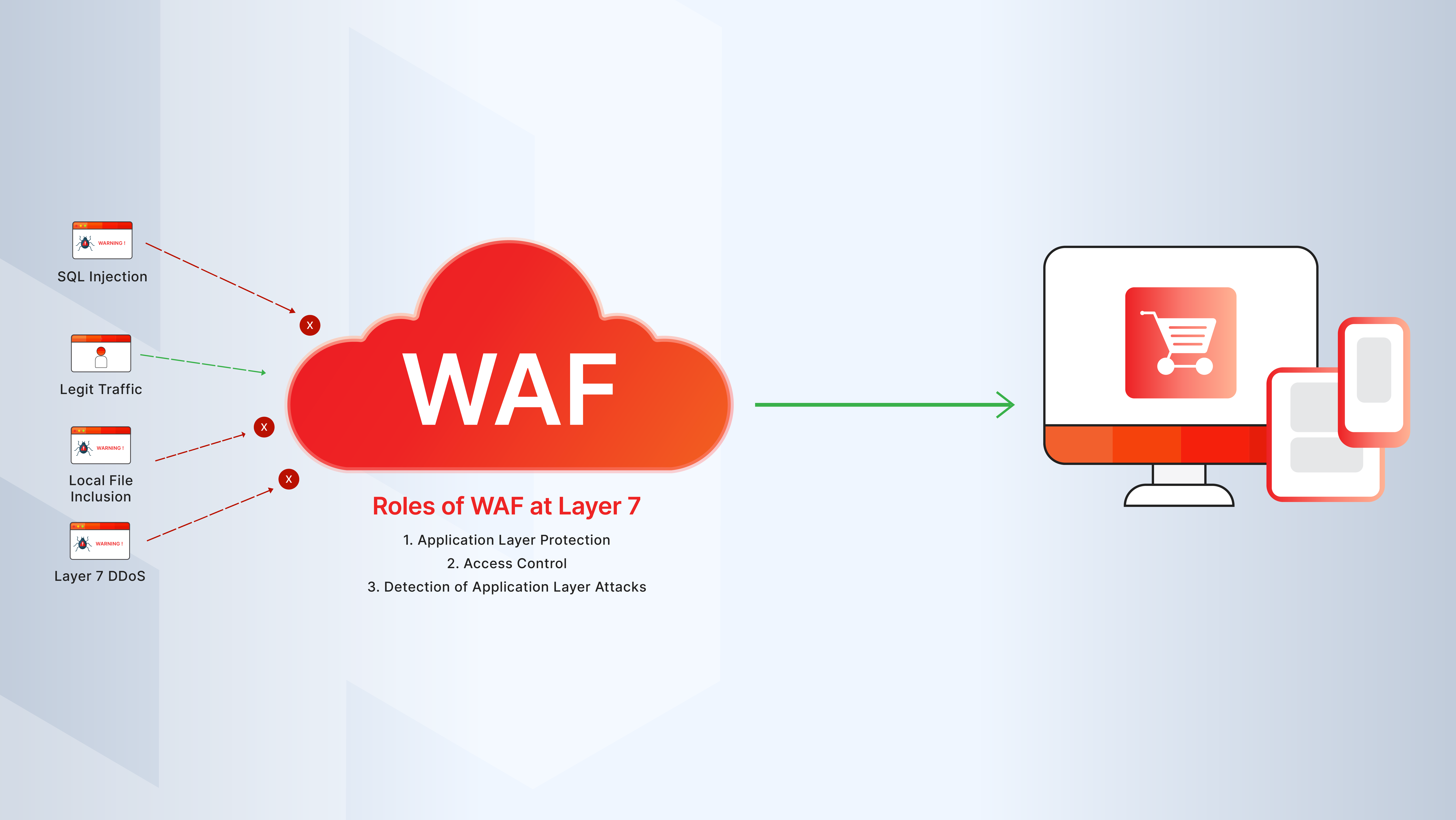
Types of Malicious Bots
Understanding bot types helps in fine-tuning WAF rules:
- Scraper Bots: Crawl your content, prices, or data to duplicate or steal information.
- Brute Force Bots: Attempt thousands of logins using credential stuffing or dictionary attacks.
- Spam Bots: Fill out forms or comment sections with unsolicited content.
- DDoS Bots: Overwhelm your server with thousands of requests, often from a botnet.
How to Block Malicious Bots with WAF
A properly configured WAF can filter harmful bot traffic effectively without disrupting real users. Here’s how:
- Activate Bot Protection Rules: Use the WAF’s built-in bot detection and mitigation features.
- Block or Rate-Limit Suspicious IPs: Automatically restrict IPs with bot-like behavior or poor reputations.
- Set Access Control Rules: Limit access to sensitive endpoints (e.g., login pages, admin panels).
- Use JavaScript or CAPTCHA Challenges: Deploy these selectively to challenge non-human clients.
- Analyze Logs Regularly: Monitor WAF logs to identify new bot patterns and update rules accordingly.
Conclusion
As bots become more sophisticated, so must your defenses. A WAF acts as a smart security layer between your application and the internet—helping you detect, classify, and block malicious bot traffic effectively. With the right configuration, your WAF can reduce server load, protect sensitive data, and ensure a safer user experience.