Introduction
Web Application Firewalls (WAFs) are essential for protecting modern web applications, but the technical jargon around them can be overwhelming. This glossary breaks down the most commonly used terms in the WAF and web security world—making it easier for developers, sysadmins, and decision-makers to navigate security conversations confidently.
Essential WAF Terms You Should Know
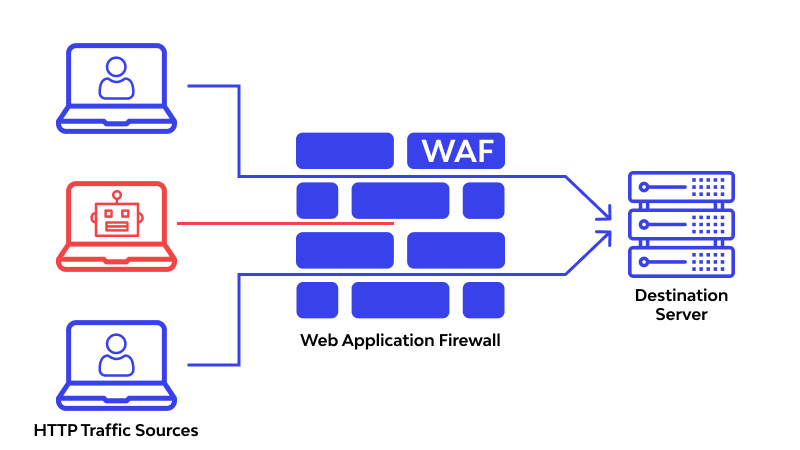
- WAF (Web Application Firewall): A security system that filters, monitors, and blocks malicious traffic to and from a web application.
- Rule Set: A collection of predefined or custom rules that determine how incoming HTTP requests should be inspected or blocked.
- False Positive: A legitimate request that is mistakenly identified as a threat and blocked by the WAF.
- False Negative: A malicious request that passes through the WAF undetected.
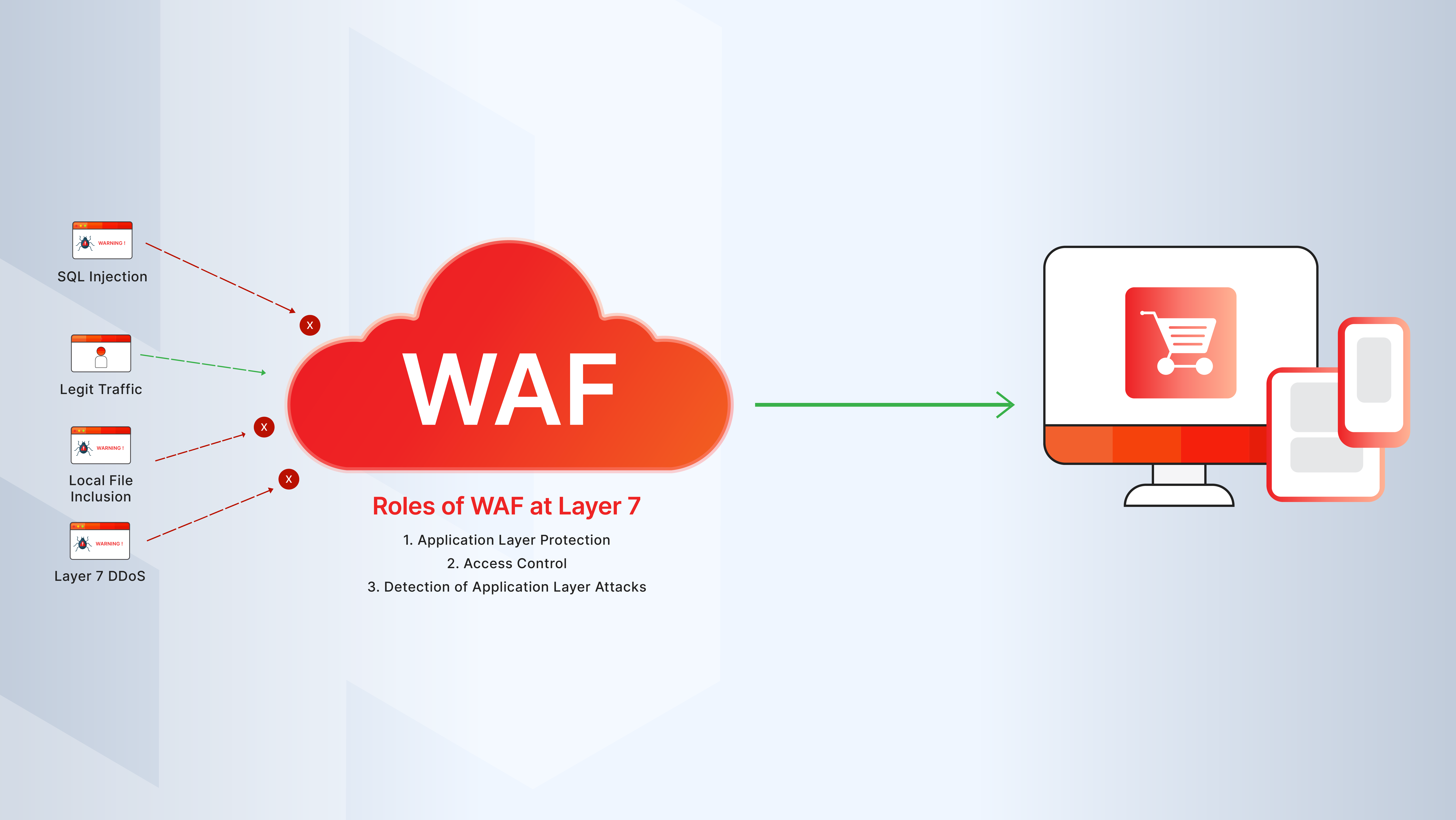
- SQL Injection: A type of attack where malicious SQL queries are inserted into form fields or URLs to manipulate databases.
- Cross-Site Scripting (XSS): A vulnerability where attackers inject malicious scripts into web pages viewed by others.
- Bot Protection: Features in WAFs that detect and block automated traffic such as credential stuffing, scraping, or denial-of-service bots.
- Geo Blocking: The ability to allow or deny traffic based on the geographical origin of the IP address.
- Rate Limiting: A technique used to restrict the number of requests a client can make in a certain time frame, protecting against brute-force and DoS attacks.
- OWASP Top 10: A list of the ten most critical web application security risks published by the Open Web Application Security Project.
- TLS Termination: The process where encrypted HTTPS traffic is decrypted by the WAF before it reaches the web server.
- Application Layer (Layer 7): The top layer in the OSI model, where HTTP(S) traffic and web application data are processed—this is where WAFs operate.
- Positive Security Model: A security approach where only explicitly allowed requests are accepted—all others are denied by default.
- Negative Security Model: A model where known bad patterns or behaviors are blocked, and everything else is allowed by default.
- Zero-Day Attack: An attack that exploits a previously unknown vulnerability for which there is no patch yet.
Conclusion
Understanding WAF-related terminology is the first step in building better web security strategies. Whether you’re a developer, a security analyst, or an IT manager, familiarizing yourself with these key concepts ensures smarter configuration, faster troubleshooting, and stronger defense against cyber threats.