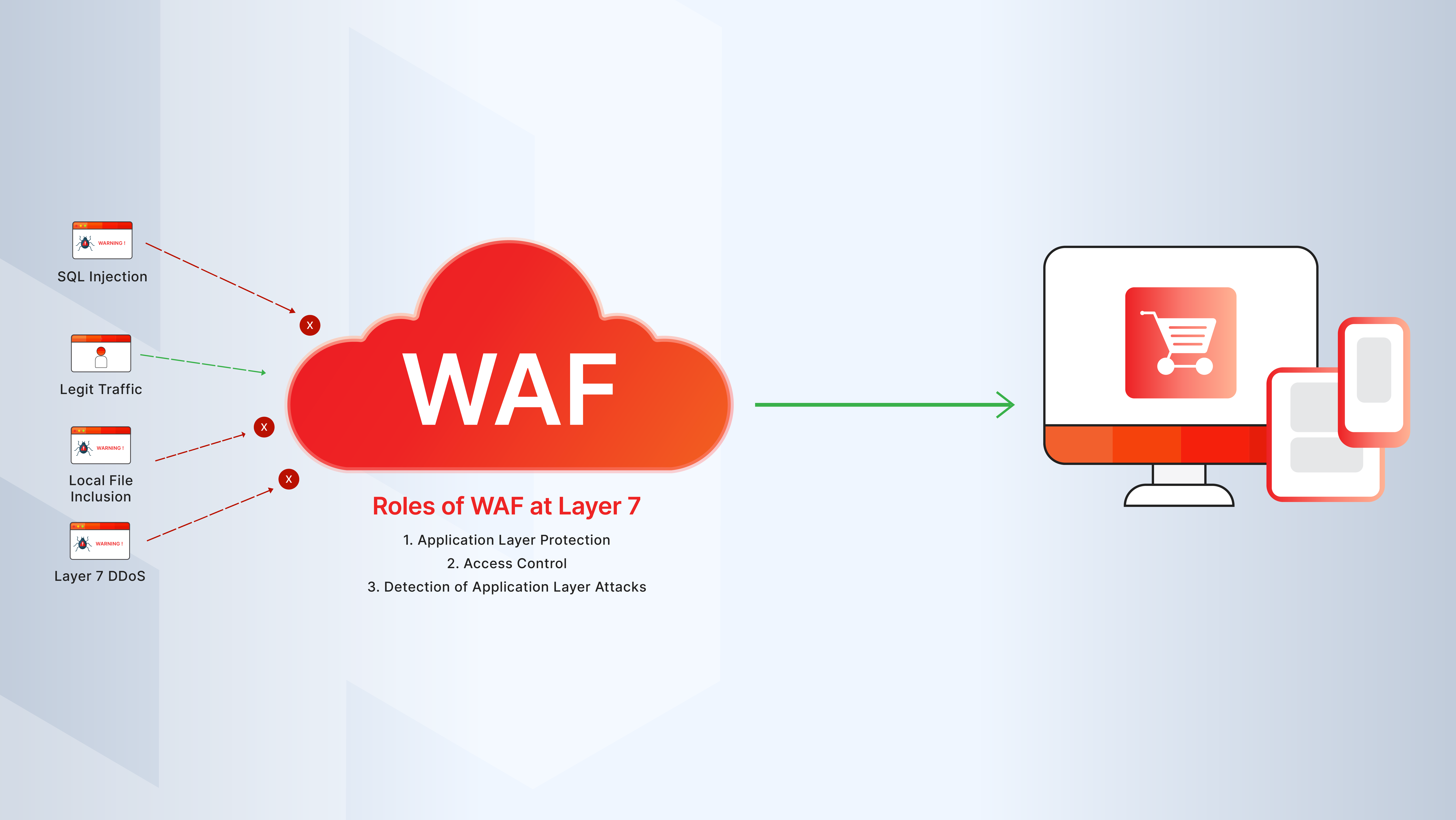
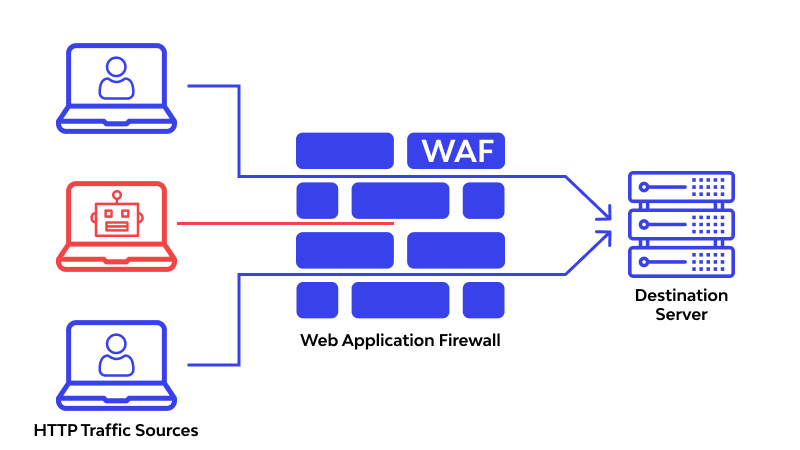
Introduction
Deploying a Web Application Firewall (WAF) is a crucial step toward protecting web applications from threats like SQL injection, XSS, and bot attacks. However, misconfigurations can leave even the best WAF ineffective—or worse, disruptive to normal operations. Below are seven of the most common mistakes made by WAF owners and how to avoid them.
1. Using Default Settings Without Customization
Most WAFs come with default rule sets that offer basic protection. However, every application is unique, and relying solely on default configurations can lead to missed threats or unnecessary false positives. Customizing the WAF to your application's structure and traffic is essential.
2. Not Enabling or Updating Threat Signatures
Outdated threat signatures leave your WAF blind to new vulnerabilities and attack vectors. Ensure that automatic updates are enabled and that your WAF is regularly synced with the latest threat intelligence feeds.
3. Overly Permissive Rules
In an effort to reduce false positives, some administrators disable or weaken WAF rules—allowing dangerous traffic to pass through. A balanced rule set that blocks malicious requests while allowing legitimate traffic is key to maintaining both security and usability.
4. Ignoring False Positives and Logs
Many WAF users ignore log files or alerts until a problem arises. However, false positives can indicate configuration issues or potential blind spots. Regularly reviewing WAF logs helps fine-tune rules and improve detection accuracy.
5. Failing to Protect APIs and Subdomains
WAFs are often deployed only for main web domains, leaving APIs, admin panels, and subdomains exposed. Ensure full coverage by configuring the WAF to inspect traffic across all entry points of your application ecosystem.
6. Not Integrating with Other Security Systems
WAFs work best when integrated with SIEM, IAM, and threat intelligence platforms. Lack of integration limits visibility and response capabilities. Connect your WAF to other tools to create a unified defense strategy.
7. Skipping Post-Deployment Testing
Deploying a WAF without proper testing can result in blocked legitimate users or missed attacks. Always perform post-deployment testing, including simulated attacks and load tests, to validate the configuration before going live.
Conclusion
Web Application Firewalls are powerful tools—but only when properly configured and maintained. Avoiding these seven common mistakes ensures that your WAF functions as an effective shield against evolving web threats. Regular monitoring, customization, and integration with your broader security stack are essential for long-term success.