Introduction
The Zero Trust security model is a modern approach to cybersecurity that assumes no user or system should be trusted by default. Instead, it enforces strict identity verification and access control across all layers of a network. Meanwhile, a Web Application Firewall (WAF) protects web applications from attacks like SQL injection, XSS, and bot traffic. When used together, WAF and Zero Trust create a robust, multi-layered defense system against today’s advanced threats.
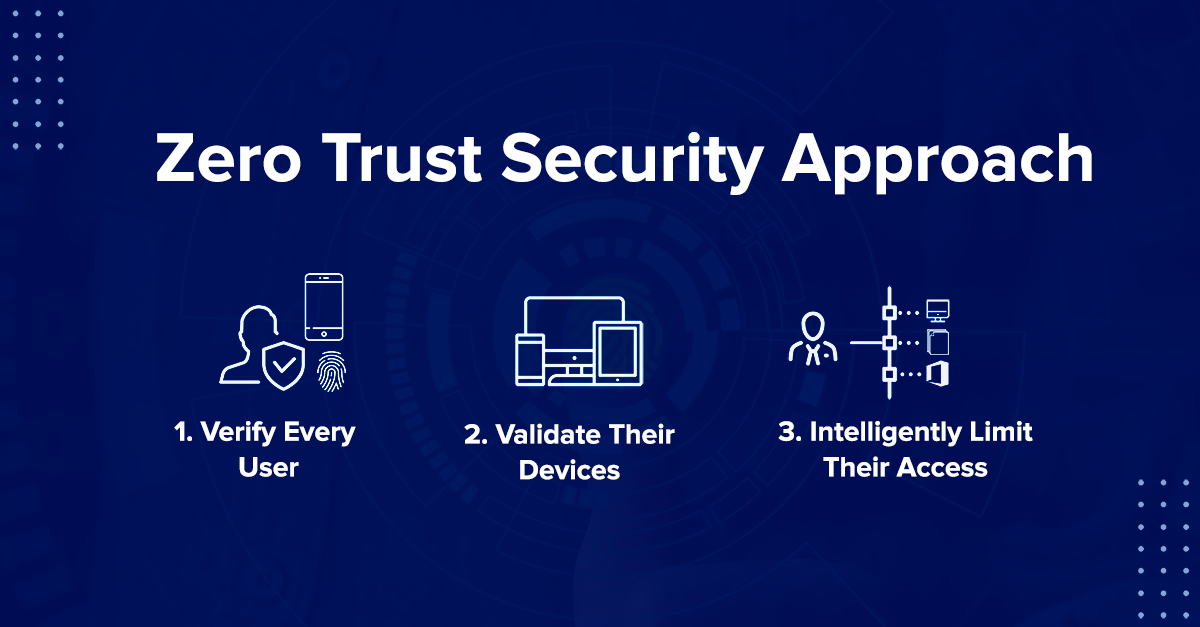
What is the Zero Trust Security Model?
Zero Trust is based on the principle of “never trust, always verify.” It treats every access attempt—internal or external—as potentially hostile. Key components of Zero Trust include:
- Strict identity and access management (IAM)
- Micro-segmentation of networks
- Continuous monitoring and logging
- Least privilege access enforcement
What is a WAF?
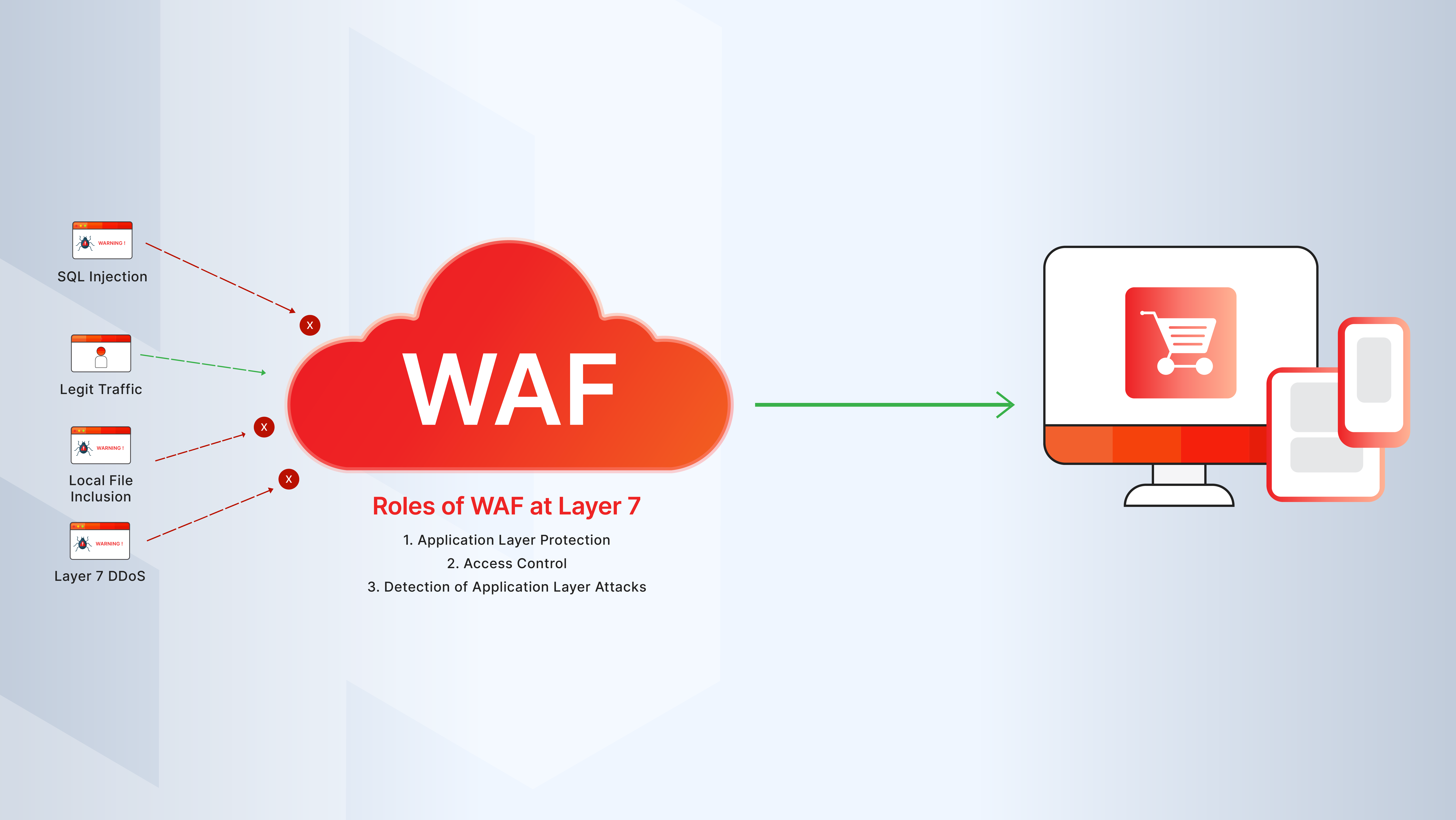
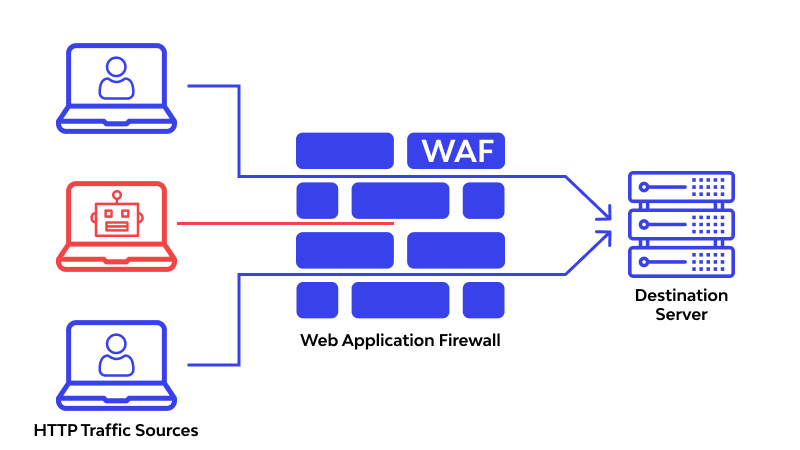
A Web Application Firewall filters, monitors, and blocks HTTP/S traffic to and from a web application. It operates at Layer 7 of the OSI model and is designed to prevent application-layer attacks like:
- SQL injection
- Cross-site scripting (XSS)
- File inclusion
- Remote code execution
- Credential stuffing and bot attacks
How WAF Supports the Zero Trust Model
WAF plays a critical role in extending Zero Trust to the application layer. Here’s how the two work together:
1. Enforcing Least Privilege at the Application Level
While Zero Trust limits network access, WAF ensures that even allowed traffic doesn’t exploit application vulnerabilities. It verifies the legitimacy of each request, applying rules and signatures to filter threats.
2. Authentication and Access Controls
WAFs can integrate with identity providers (IdPs) and access management tools to enforce login and authentication policies before a request reaches the application, reinforcing Zero Trust authentication.
3. Micro-Segmentation for Web Services
Zero Trust segments network zones. A WAF can help segment and protect specific APIs or microservices by applying tailored security rules, reducing lateral movement across applications.
4. Real-Time Threat Detection
WAFs monitor traffic in real time, identifying anomalies or known attack patterns. This continuous inspection aligns with Zero Trust’s principle of constant verification and behavioral monitoring.
5. Logging and Auditing
Zero Trust emphasizes complete visibility. WAFs log all traffic and can integrate with SIEM (Security Information and Event Management) systems for centralized analysis, supporting Zero Trust observability.
Benefits of Combining WAF with Zero Trust
- Stronger protection against both external and internal threats
- Improved application-level visibility and traffic control
- Reduces attack surface at the web layer
- Better compliance with data protection and privacy regulations
Conclusion
Zero Trust is not a single product but a comprehensive strategy. By integrating a WAF into a Zero Trust architecture, organizations gain critical protection at the application layer—where many modern attacks occur. Together, they create a defense-in-depth approach that aligns with today's security needs and helps prevent breaches before they occur.