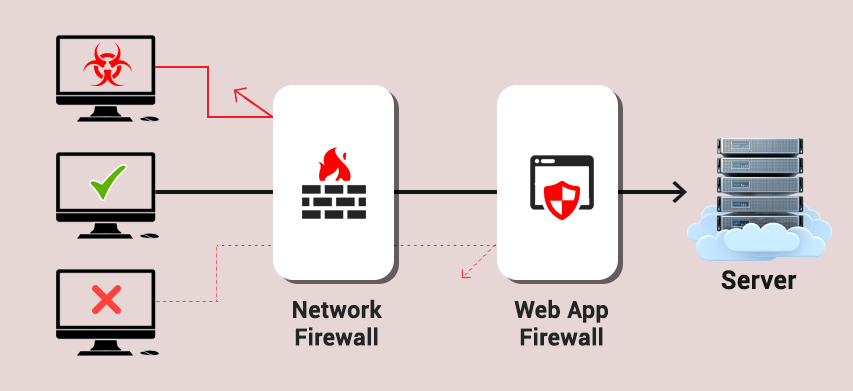
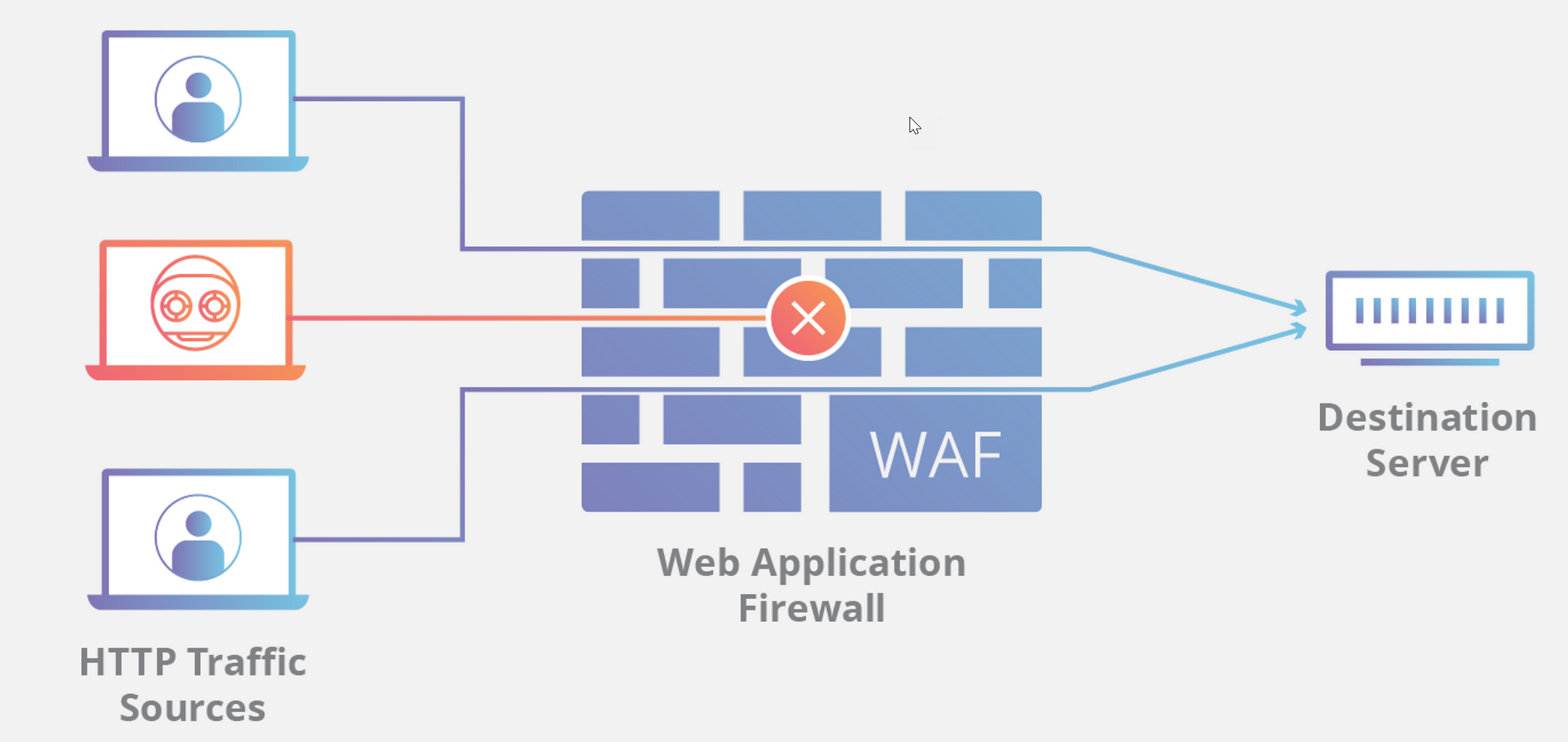
Introduction
WAF logs are one of the most valuable tools for understanding and enhancing the security of your web application. However, these logs can be overwhelming without the right context. Learning how to read and analyze WAF logs allows developers and security teams to detect attacks, reduce false positives, and improve application resilience.
What Are WAF Logs?
WAF logs are detailed records of HTTP requests that were evaluated, blocked, or allowed by a Web Application Firewall. Each log entry typically contains metadata such as timestamp, IP address, request URI, request method, rule triggered, and action taken (e.g., blocked or allowed).
Key Elements Found in WAF Logs
- Timestamp: When the request occurred
- Client IP: The source IP address of the request
- Request URI: The path or resource being accessed
- HTTP Method: The method used (GET, POST, etc.)
- Rule ID / Rule Name: The specific WAF rule that was triggered
- Action Taken: What the WAF did (Block, Allow, Challenge, etc.)
- User-Agent: The device or browser making the request
Common Indicators in WAF Logs
- Repeated Requests from the Same IP: Could indicate a bot or automated scan
- Rule Triggers on SQL Keywords: Suggests SQL injection attempts
- Abnormal User-Agents: Might be a scraper or exploit tool
- High Rate of 403 Errors: Indicates the WAF is actively blocking requests
How to Analyze WAF Logs
1. Use Log Aggregation Tools
Tools like ELK Stack (Elasticsearch, Logstash, Kibana), Datadog, or Splunk help centralize and visualize WAF logs for easier analysis.
2. Filter by Rule Actions
Separate blocked requests from allowed traffic to focus on potential threats first.
3. Look for Patterns
Track patterns over time—same IPs, repeated payloads, or targeting specific endpoints—these could point to coordinated attacks or scanning tools.
4. Correlate with Application Logs
Compare WAF logs with application logs to validate if blocked requests were legitimate or false positives.
Best Practices for Interpreting WAF Logs
- Regularly review logs, especially after rule updates
- Create custom alerts for high-severity triggers
- Whitelisting trusted sources to reduce noise
- Document and tune rules to reduce false positives
Conclusion
Understanding WAF logs is essential for maintaining a secure and functional web application. By learning to interpret these logs, developers and security teams gain valuable insights into traffic behavior, attack attempts, and WAF effectiveness. Regular log analysis not only improves protection but also enhances application performance and user experience.