What is DDoS Protection and How to Prevent It?
In today's digital age, Distributed Denial of Service (DDoS) attacks have become one of the most common threats to websites and online services. A DDoS attack occurs when multiple compromised devices flood a target server or network with excessive traffic, making it unavailable to legitimate users. This can result in downtime, loss of revenue, and damage to reputation.
Why DDoS Protection is Important
DDoS protection refers to strategies and tools designed to detect, mitigate, and prevent DDoS attacks. Without adequate protection, websites and networks remain vulnerable to traffic overload, which can cripple online services. Effective DDoS protection ensures continuous availability and a seamless user experience.
Common Types of DDoS Attacks
Volumetric Attacks: Overwhelm the bandwidth of the target by flooding it with massive amounts of data.
Protocol Attacks: Exploit weaknesses in network protocols to exhaust server resources.
Application Layer Attacks: Target specific applications or services with seemingly legitimate traffic.
How to Prevent DDoS Attacks
Use a Content Delivery Network (CDN): CDNs distribute traffic across multiple servers globally, reducing the impact of traffic surges.
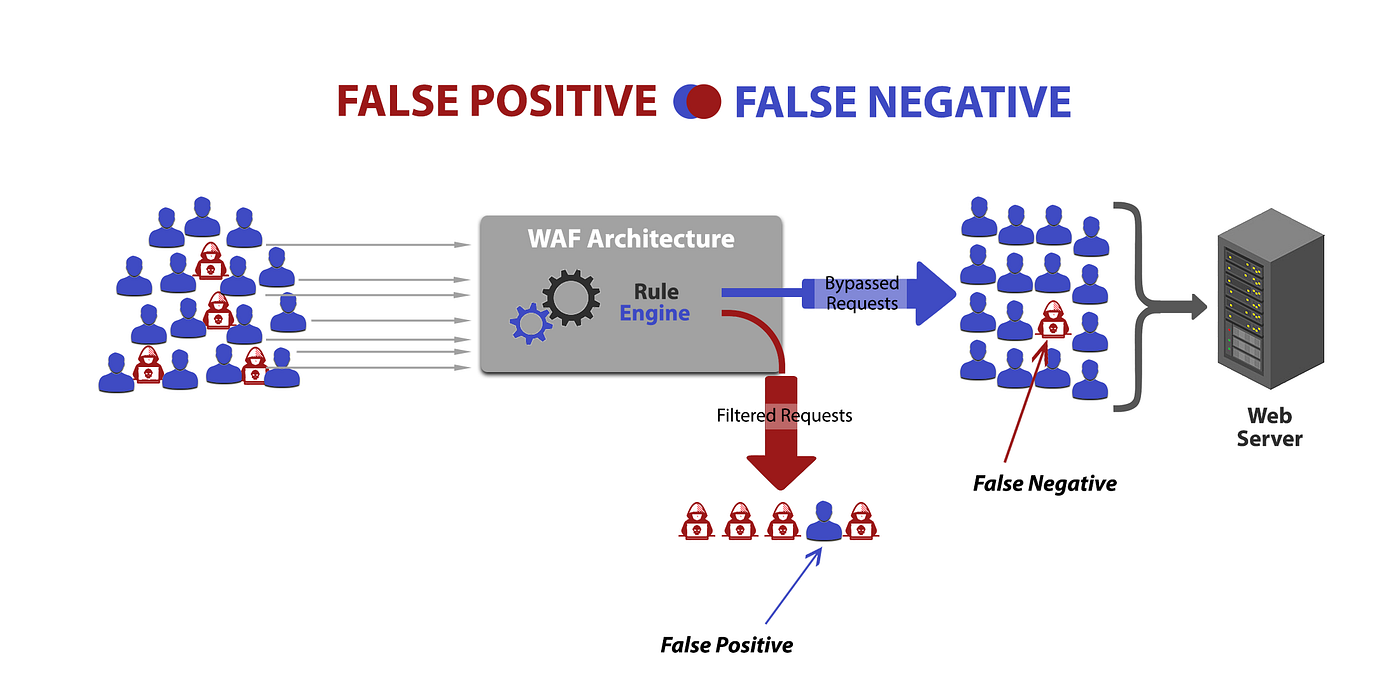
Implement Firewalls and Intrusion Prevention Systems (IPS): These tools monitor traffic patterns and block suspicious activities.
Rate Limiting: Limit the number of requests from a single IP address to avoid overload.
Traffic Filtering and Analysis: Use specialized tools to analyze and filter out malicious traffic in real-time.
Keep Systems Updated: Regularly update software and hardware to patch known vulnerabilities.
Work with Your Hosting Provider: Many providers offer built-in DDoS mitigation services.
Conclusion
DDoS attacks pose a serious risk to online platforms, but with proper protection strategies, their impact can be minimized. Combining multiple defense layers such as CDNs, firewalls, and real-time monitoring is the best approach to safeguard your website or network from these attacks.